Checking Out the Different Kinds Of IT Managed Solutions to Enhance Your Operations
Network Management Provider
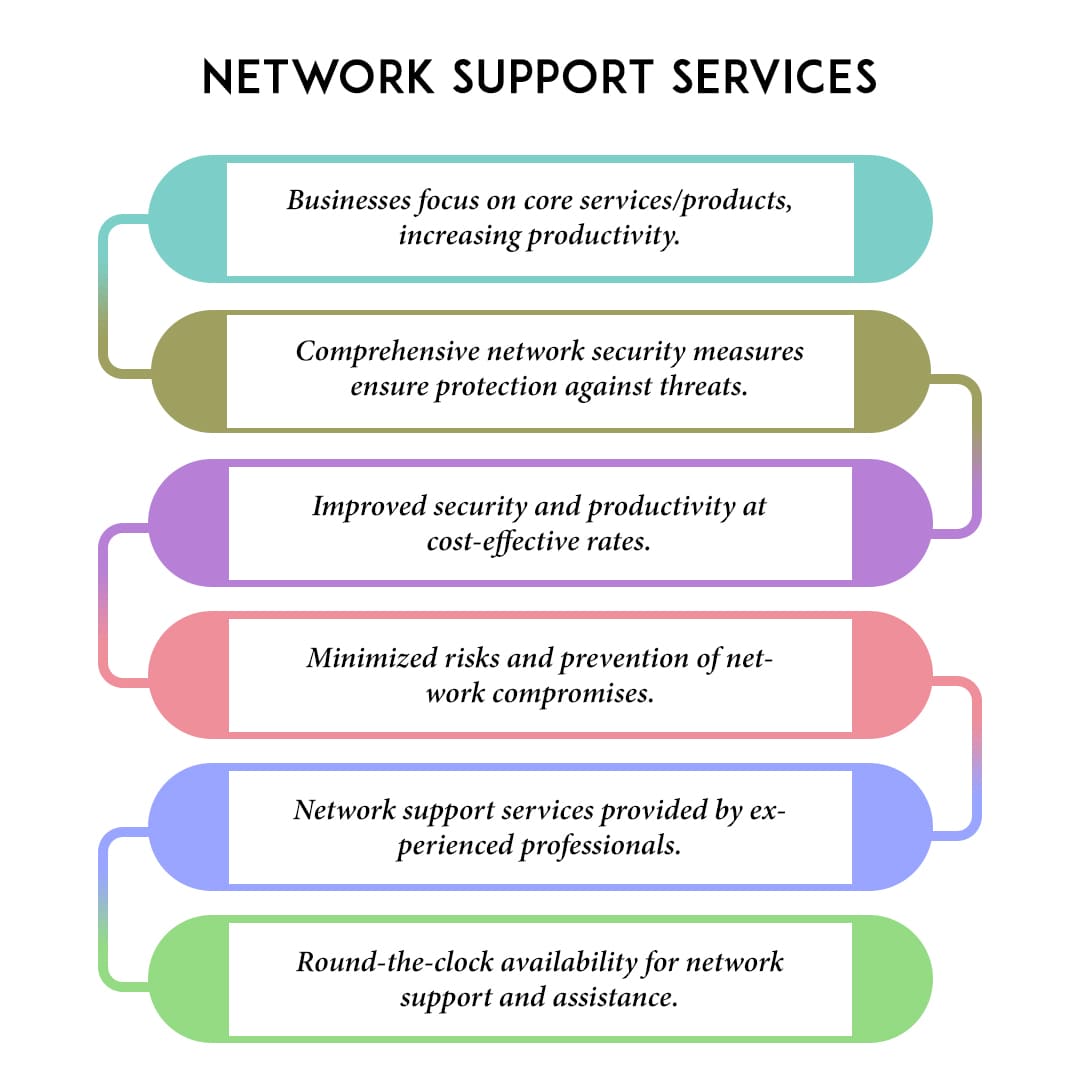
Network Management Services play a crucial duty in guaranteeing the performance and reliability of an organization's IT facilities. These solutions encompass a variety of tasks targeted at preserving optimum network performance, reducing downtime, and proactively resolving possible problems prior to they escalate.
A detailed network administration approach consists of checking network traffic, taking care of data transfer use, and making sure the accessibility of critical sources. By employing innovative tools and analytics, companies can obtain understandings into network performance metrics, enabling educated decision-making and critical preparation.
Furthermore, reliable network monitoring involves the setup and maintenance of network gadgets, such as firewall programs, routers, and switches, to ensure they operate seamlessly. Normal updates and spots are vital to secure against vulnerabilities and enhance functionality.
Additionally, Network Administration Services often consist of troubleshooting and assistance for network-related concerns, making sure fast resolution and marginal interruption to service procedures. By contracting out these services to specialized providers, organizations can focus on their core expertises while gaining from professional support and assistance. Generally, reliable network monitoring is essential for achieving functional quality and cultivating a durable IT environment that can adapt to developing business needs.
Cybersecurity Solutions
In today's electronic landscape, the security of sensitive information and systems is vital as organizations progressively rely upon innovation to drive their operations. Cybersecurity services are vital components of IT handled services, developed to guard an organization's digital possessions from developing dangers. These services include a range of methods, tools, and methods aimed at mitigating risks and resisting cyberattacks.
Crucial element of efficient cybersecurity options consist of danger discovery and reaction, which make use of innovative monitoring systems to identify prospective safety violations in real-time. IT managed solutions. Furthermore, regular susceptability assessments and infiltration screening are carried out to reveal weaknesses within a company's facilities prior to they can be exploited
Applying durable firewall softwares, intrusion discovery systems, and file encryption methods further strengthens defenses versus unauthorized accessibility and data breaches. Furthermore, detailed staff member training programs concentrated on cybersecurity awareness are critical, as human error remains a leading root cause of safety incidents.
Eventually, buying cybersecurity options not only protects delicate data but additionally boosts organizational strength and count on, ensuring compliance with regulatory standards and maintaining an one-upmanship in the marketplace. As cyber risks remain to progress, focusing on cybersecurity within IT managed services is not just sensible; it is necessary.
Cloud Computer Provider
Cloud computer solutions have revolutionized the means organizations take care of and store their information, offering scalable remedies that enhance operational performance and versatility. These services permit businesses to gain access you can try these out to computing resources online, eliminating the need for substantial on-premises infrastructure. Organizations can choose from different versions, such as Framework as a Service (IaaS), System as a Solution (PaaS), and Software Program as a Solution (SaaS), each accommodating different operational demands.
IaaS provides virtualized computing resources, allowing companies to scale their framework up or down as called for. PaaS promotes the growth and deployment of applications without the inconvenience of taking care of underlying hardware, enabling programmers to focus on coding instead than framework. SaaS delivers software program applications by means of the cloud, making sure customers can access the most up to date variations without manual updates.
Moreover, cloud computing boosts collaboration by making it possible for real-time access to shared applications and resources, despite geographic area. This not just promotes synergy but additionally speeds up task timelines. As businesses continue to accept electronic improvement, adopting cloud computing services comes to be vital for enhancing procedures, lowering prices, and driving innovation in a significantly competitive landscape.
Help Desk Support
Assist desk assistance is an important part of IT handled services, giving companies with the essential assistance to settle technical problems effectively - Enterprise Data Concepts, LLC. This service acts as the first point of contact for workers facing IT-related obstacles, making sure marginal disruption to performance. Aid workdesk support incorporates numerous functions, including fixing her latest blog software and equipment problems, assisting individuals via technological procedures, and addressing network connection problems
A well-structured help desk can run through several channels, consisting of phone, e-mail, and live chat, enabling individuals to choose their favored method of interaction. This versatility boosts customer experience and guarantees prompt resolution of concerns. Aid workdesk assistance often uses ticketing systems to track and manage demands, allowing IT teams to prioritize jobs efficiently and keep track of performance metrics.
Information Back-up and Recuperation
Reliable IT managed services prolong beyond prompt troubleshooting and support; they also include robust data backup and recuperation solutions. Managed solution suppliers (MSPs) provide detailed information back-up techniques that generally include automated back-ups, off-site storage space, and routine testing to ensure data recoverability.

In addition, effective recovery solutions go together with backup methods. A reliable recovery strategy ensures that organizations can recover data swiftly and precisely, hence preserving functional continuity. Routine drills and analyses can better enhance recuperation preparedness, furnishing organizations to navigate information loss scenarios with confidence. By executing durable information back-up and recovery services, companies not only secure their data yet additionally boost their general durability in a significantly data-driven globe.
Verdict
In final thought, the application of numerous IT handled solutions is vital for boosting operational performance in contemporary companies. Network management solutions make sure ideal infrastructure efficiency, while cybersecurity services protect delicate info from possible threats. Cloud computer solutions promote adaptability and cooperation, useful source and help desk assistance supplies immediate help for IT-related challenges. Additionally, information backup and healing services shield organizational information, guaranteeing swift reconstruction and cultivating resilience. Collectively, these solutions drive advancement and operational excellence in the electronic landscape.
With a variety of offerings, from network monitoring and cybersecurity solutions to cloud computing and assistance desk support, companies should meticulously evaluate which solutions straighten ideal with their functional demands.Cloud computing services have changed the way organizations manage and keep their information, offering scalable services that boost functional performance and versatility - Enterprise Data Concepts, LLC. Organizations can pick from different models, such as Facilities as a Service (IaaS), System as a Solution (PaaS), and Software Program as a Solution (SaaS), each catering to various operational demands
Efficient IT took care of services extend beyond prompt troubleshooting and support; they additionally incorporate robust information back-up and recuperation services. Managed service providers (MSPs) use extensive data backup techniques that usually include automated back-ups, off-site storage, and routine testing to guarantee information recoverability.
 Jake Lloyd Then & Now!
Jake Lloyd Then & Now! Jason J. Richter Then & Now!
Jason J. Richter Then & Now! Hailie Jade Scott Mathers Then & Now!
Hailie Jade Scott Mathers Then & Now! Catherine Bach Then & Now!
Catherine Bach Then & Now! The Olsen Twins Then & Now!
The Olsen Twins Then & Now!